On June 22,2021, news broke that LinkedIn, after being a victim of a data leak of 500 million users, was once again left red-faced after a hacker claimed to have data of 700 million users. The hacker going by the name “God User” was looking to sell the data of these 700 million users on RaidForums. As a way to prove that the hacker really did have all of this information, data of 1 million users was posted on RaidForums.
This however took a turn when all of this data was leaked online this week. The files are being shared on a private telegram channel taking the form of a torrent file of approximately 187 GB of information.
The Record was able to obtain a copy of this file and upon initial analysis found that the information in the files included users’ names, their linkedin IDs, profile URLs, location and email addresses.
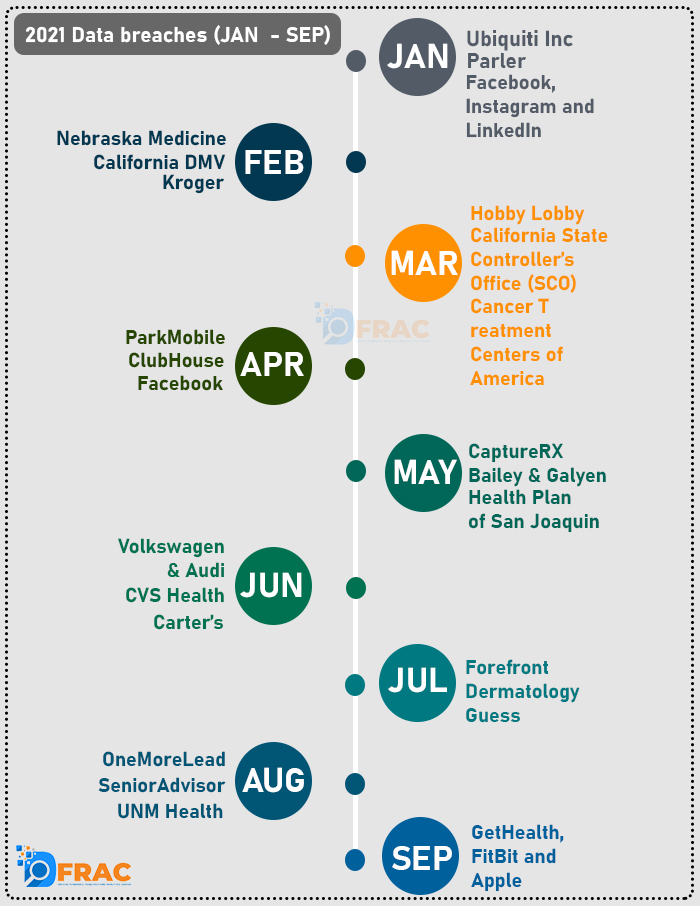
Data scraping of this sort is becoming incredibly common in the last few months. Facebook in April,2021 had to acknowledge that data of over 500 million users was scraped from its server. Data of 235 million users from Instagram, Youtube and TikTok was leaked last years and the frequency of these leaks are only increasing.
The Record however found that in the case of this leak, the information gathered of the users were already publicly available. The only thing that might be difficult to obtain by any individual would be the email IDs of the users.
However, this leak did not contain email addresses of all 700 million users rendering more of the data of no use.
LinkedIn is perhaps not liable for the extraction of basic user information that is already publicly available on their website, however the fact that someone was able to scrape the information of 700 million users is alarming.
This puts the users in jeopardy because essentially nobody is taking the blame for such a breach neither the company and definitely not the hacker over even the messaging platforms used to host and send the data.
How is this data even used? Most of the data even though it is available in the public domain could be used to create Open Source Intelligence Network Databases which when grouped together with other information about the users based on their email IDs can be used for ransom and the data can be held hostage.