On September 29,2021, the US Department of Justice issued a federal indictment in the Northern District of Illinois against a Turkish individual named Izzet Merk Ozek. Ozek is a citizen of Turkey and the indictment accused him of launching a cyber attack on a Chicago based multinational company in the year 2017.
According to the indictment Ozek is accused of using a defunct malware botnet called WireX to launch a hoard of denial of service DDoS attacks on the company’s server.
DDoS attacks are cyberattacks launched on a server to misdirect the service provided by the owner away from their intended users. A simple way to understand this would be for example you are trying to book movie tickets online on a ticketing website, now when you try to book your tickets, the links misdirect you to other websites that have nothing to do with your tickets.
You could also possibly see that all the seats for the movie are booked but in reality they have just all been filled up with bots unbeknownst to the host company. This is the rough explanation of what a DDoS attack is like.
Now what are botnets? As we know, bots are automated software applications that are capable of performing tasks on their own as per their code. A botnet is a device that hosts hundreds and thousands of these bots in one place awaiting their command. A botnet is used to send spam and mostly to conduct criminal activities such are stealing data and of course, DDoS attacks.
Ozek used a defunct malware botnet called WireX but it is unclear whether he made the bot himself or took it from someone. Authorities say that his attacks infected android smartphones and sent large amounts of traffic to the company’s booking services and servers causing their server to crash.
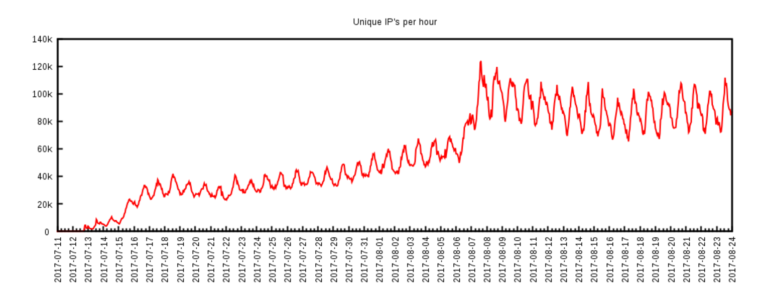
According to the sources, WireX at its peak had over 1,20,000 bots at the users’ disposal which is a massive amount. Tracking it was not easy, but soon after the attack took place, several companies including Akamai, Cloudflare, Flashpoint, Google, Dyn, RiskIQ, and Team Cymru came together to trace the botnet and eventually take control of its servers. You can read more about how they tracked it in detail here.